Did you know that hackers are now directly targeting backups? They’re no longer only targeting servers, corporate systems, or business-critical applications. According to a Sophos study, attackers have attempted to compromise backups in over 94% of ransomware attacks. Over half of those attacks (57%) were successful, greatly undermining an organization’s ability to recover data.
Ensuring the security of their backups is now a top priority for enterprises. This is where offline backups come in. With offline backups, data is physically disconnected from the network, so ransomware cannot access the backups, thus establishing a line of defense against ransomware.
Physical isolation is a capable method of securing your data. However, it is neither cost-efficient nor efficient for accessing data. As businesses’ data needs evolve, modern offline backup methods have emerged. It’s important to balance security and usability when planning your backup infrastructure.
Transitioning from physical isolation to logical isolation
In the past, physical isolation was used as a way to store offline backups to ensure data security.
Physically air-gapping your data meant that the network was manually disconnected or powered down so that the device was completely offline. Physical air gaps also referred to backup media such as tapes as they were physically stored at off-site locations. This way, the data was physically separated from the main system. This meant that the data was completely out of reach, unless the attacker was able to physically access the device.
However, physical isolation also comes with multiple challenges, including maintenance difficulties, dependence on human operations, being prone to human errors, and difficulties verifying backup recoverability.
To address these challenges, modern offline backups are now shifting towards logical isolation. Even though the backup systems are still connected to the network, there are multiple layers to ensure data security. This includes: authentication mechanisms, access controls, and encryption safeguards to prevent data leaks. Immutable backups also prevent data tampering or deletion, while firewalls restrict external access to data. Logical air-gapping is much more flexible, manageable, and scalable than physical isolation.
| Physical isolation | Logical isolation | |
|---|---|---|
| Isolation method | Physical disconnection: Unplugging the network, removing tapes, or turning the device off to completely separate data from the network. |
Logical disconnection: The device is still connected to the network. However, data is isolated via access controls, encryption, or firewalls. |
| Security | Complete isolation: Attackers must have physical access to the device in order to tamper with it. |
Leverage a multi-layered security approach for robust data protection |
| Management | Remote management is not possible, making remote devices difficult to access. | Remote management is possible via the internet, making management more efficient. |
| Maintenance | Manual maintenance makes operations difficult and requires dedicated personnel. | Automated systems reduce the burden of IT personnel. |
Traditional methods of physically isolating your data ensured complete separation and isolation of data but at the cost of convenience and efficiency. In comparison, with the modern method of logically isolating your data, you can balance management ease along with data protection. When looking to establish an effective offline backup strategy, businesses don’t necessarily have to choose between one or another. They can flexibly combine both approaches to meet operational needs.
Leverage physical and logical isolation with ActiveProtect
As enterprises look for data security and efficiency when implementing a data isolation solution, Synology ActiveProtect comes with both physical and logical air-gapping capabilities to provide businesses with a total solution.
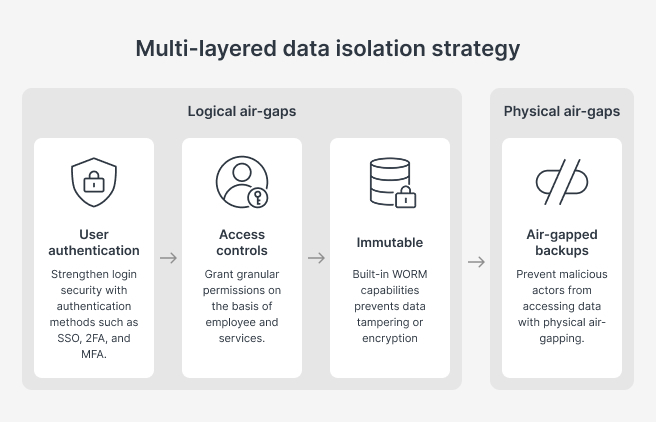
ActiveProtect provides three layers of defense to isolate data at the strictest level, even under network conditions.
User authentication: Integrate Windows AD and LDAP to centralize user management. Leverage multi-layer authentication methods such as SSO, two-factor authentication (2FA), and multi-factor authentication (MFA) to enhance login security and prevent unauthorized logins.
Role-based access controls: Use role-based access controls to implement granular permissions based on employee roles and needs, prevent privilege abuse, and ensure that only users with access can perform authorized actions.
Immutable data protection: With built-in Write Once, Read Many (WORM) technology and intelligent version-level locking, data cannot be changed, deleted, or encrypted until the data retention period ends. Even under a ransomware attack, data is intact and accessible.
How ActiveProtect optimizes physical isolation
In terms of physical isolation, ActiveProtect comes with powerful data isolation methods to provide the strictest level of data isolation and optimizes challenges associated with the traditional method of physically isolating your data. With data transmissions controls and automated isolation capabilities, you can thoroughly protect your data with ActiveProtect.
When data is transmitted from the backup server to an off-site location, the system restricts the source itself. Only authorized servers can perform data transmissions. Those without authorization won’t have access to the data, so it remains secure and isolated.
Unlike the traditional method of physically isolating data, which requires manually disconnecting and shutting down devices, companies can rely on a fully automated isolation method with ActiveProtect.
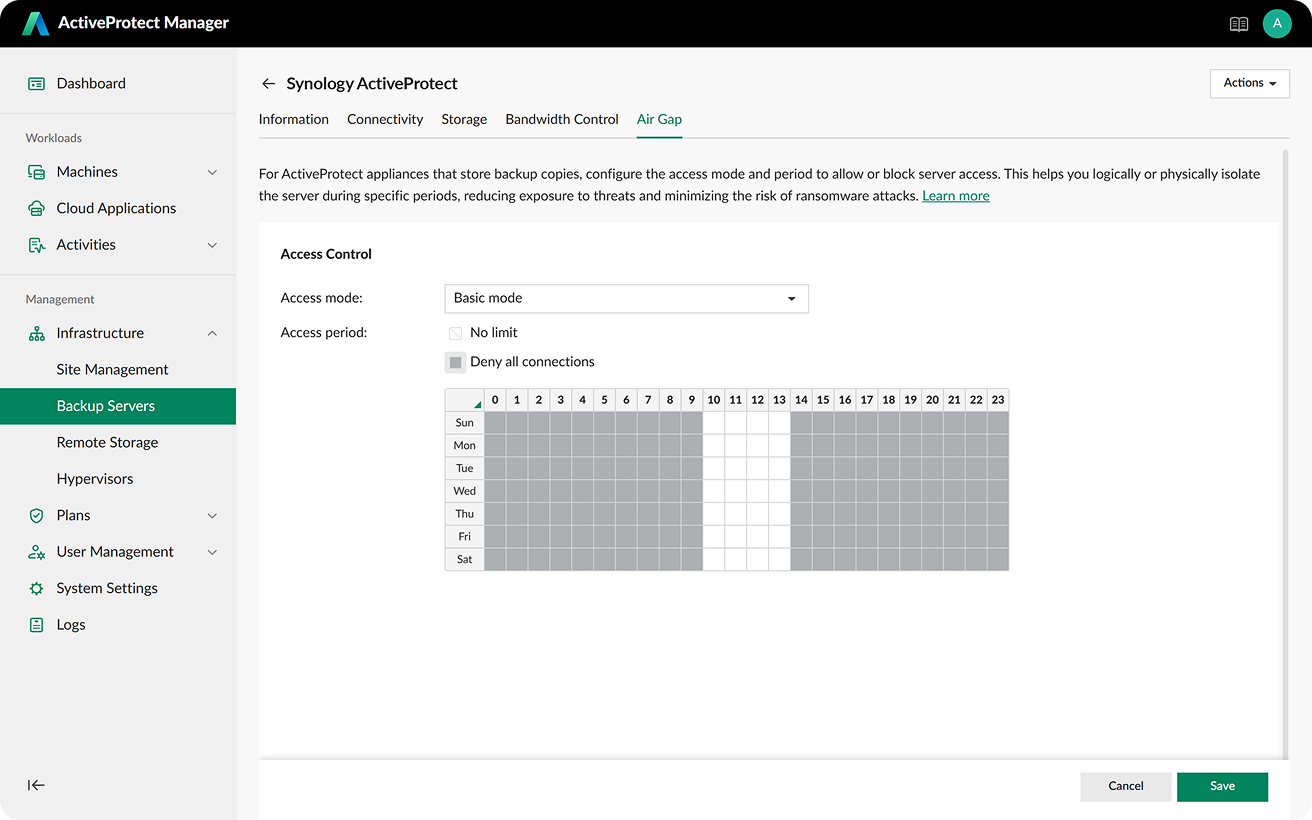
Businesses can set their data transmission times according to their schedule. During non-data transmission time periods, the backup appliances can be completely isolated by shutting down the network interface or by shutting down. If backups are completed ahead of schedule, the appliances revert to isolation mode automatically. This minimizes exposure time, leaving hackers with little opportunity to strike.
A major drawback of traditional physical air-gaps is that users are unable to access management tasks once the environment is completely disconnected from the network. As ActiveProtect separates the management port from the data port, the management port itself is in a secure, isolated network. This means that even if data ports are closed and the data is fully isolated, IT teams are able to run daily updates, daily maintenance, and recovery drills within a protected environment.
With an increase of malware targeting backups, ActiveProtect allows businesses to take advantage of both physical or logical backups to establish a safer, robust data protection infrastructure.
Click here to find out more about Synology ActiveProtect.