Encryption has a storied history, from simple substitution ciphers during the warring eras of Ancient Rome, to Mary, Queen of Scots’ ill-fated Babington Plot, and the unbreakable Navajo code that helped secure Allied communications in World War II. These pivotal moments demonstrate the enduring importance of secure communication across eras.
What is Encryption?
As the Grecian roots of the word suggest—where “en” means “in” and “kyrptos” stands for “secret”—encryption aims to secure data against unauthorized parties by turning messages unreadable and undecipherable. It is one of the oldest and most common forms of data protection. While the underlying principles remain constant, encryption implemented today has dramatically evolved to meet modern demands.
Modern Encryption
With only a single key required for encryption and decryption, symmetric encryption is one of the most commonly used encryption methods today. It requires that the key must also be kept safe (in transit), but it is significantly faster and better for bulk data transmission. Despite its relative simplicity, symmetric encryption is still highly effective against persistent, brute-force attacks. One example is the Advanced Encryption Standard (AES), adopted by the United States for classified data, which includes multiple rounds of complex transformations and cipher optimizations.
In asymmetric encryption, two different keys (“public key” for encryption; “private key” for decryption) exist, and even more computational power is needed, which makes it slower and more complex to implement, but it is considered the safer, modern methodology suitable for smaller files that need to be distributed to multiple people. One example is the ECC Curve25519, an algorithmic function that, by design, efficiently generates keys resistant to timing attacks by leveraging the properties of elliptic curves.
As encryption becomes ubiquitous in the applications you use, it is essential to recognize its different forms and implications in dealing with your data.
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Keys | Single | Public + private keys |
| Use case | Bulk data encryption | Secure key exchange |
| Example | AES-256 | ECC Curve25519 |
Encryption in Everyday Life
From online banking and e-commerce to secure messaging and healthcare records, encryption plays a vital role in protecting our sensitive information. For instance, HTTPS ensures secure connections for websites, while end-to-end encryption safeguards private communications. As encryption becomes more integral to our daily lives, users often assume it guarantees complete privacy, though that might not always be the case.
When applications claim to provide true privacy, it is important to scrutinize their methods. Not all encryption implementations are created equal, and it is important to understand the often nuanced distinctions between different types of encryption and the potential vulnerabilities and limitations of their methods for informed decision-making.
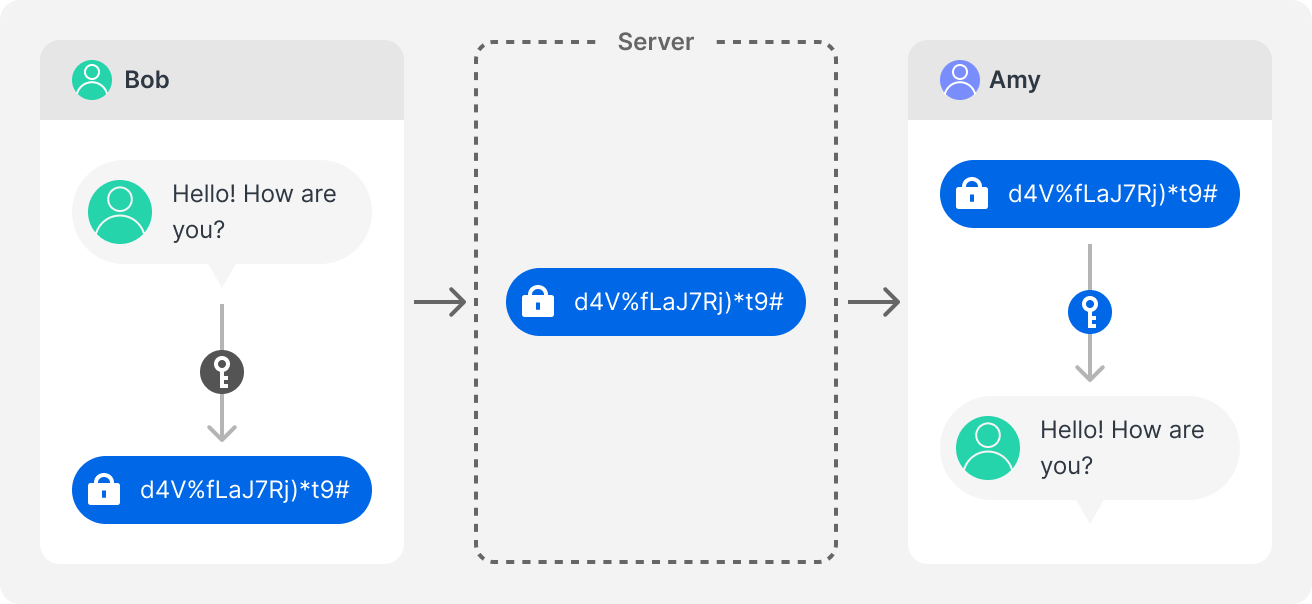
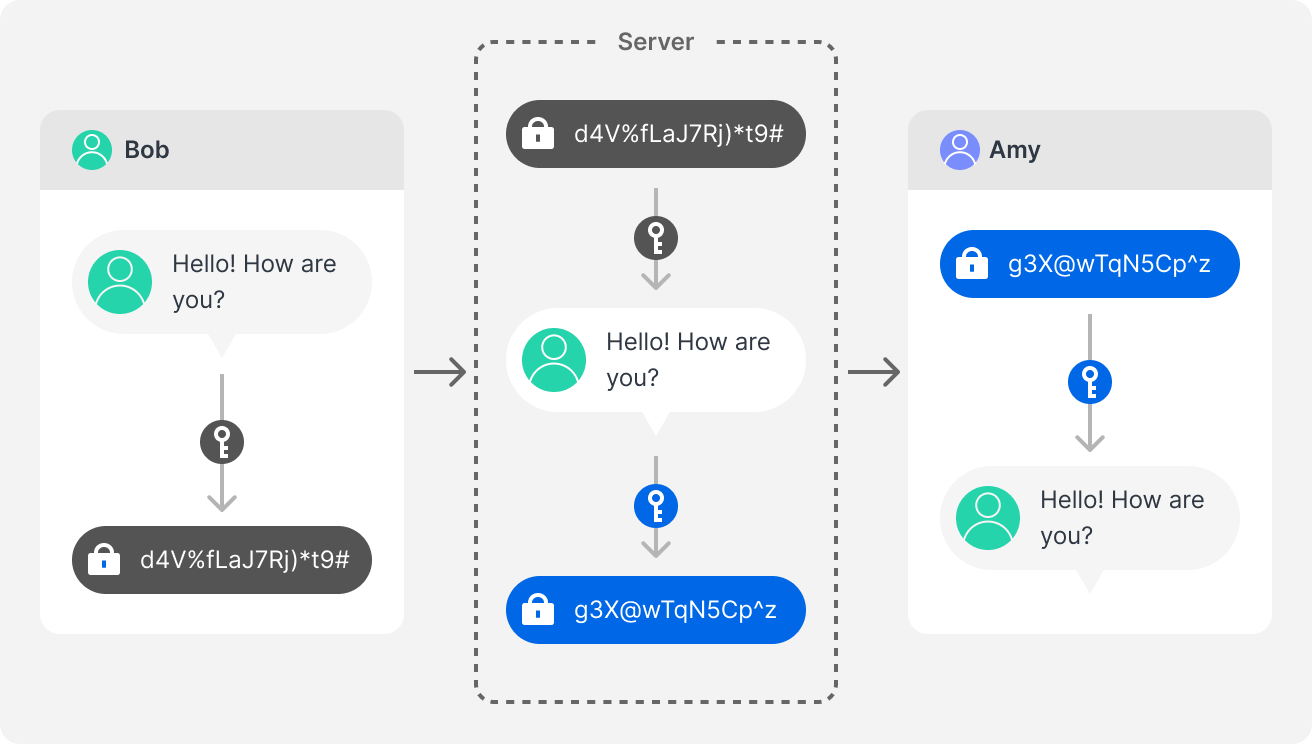
We may think that encryption means we users hold the keys to decrypt our messages, but in fact, many applications and services only implement partial or less effective forms, such as server-side encryption, where the encryption keys are left in the hands of the service provider, possibly introducing third-party access or unwanted data exposure.
End-to-end encryption that is marketed and widely believed to be how messages work
Server-side encryption
Synology and Data Privacy
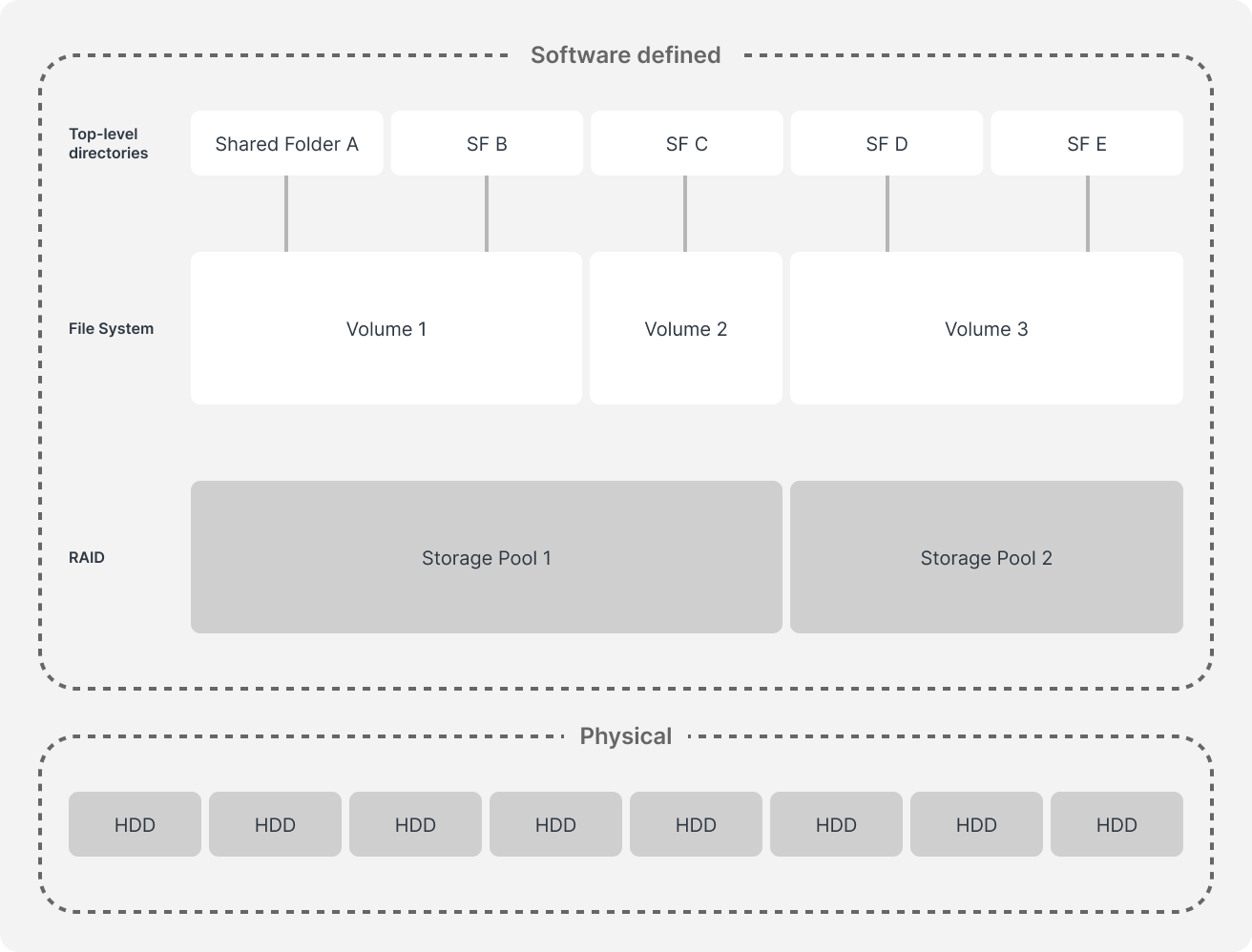
Synology embeds data protection at multiple levels, from volumes to shared folders, the encryption framework ensures that sensitive data is fully protected with encryption keys that are generated, stored, and managed securely on the device itself or through trusted external vaults.
A volume is a logical storage unit within a storage pool, and at least one volume must be created before you store data. Volume encryption on DiskStation Manager (DSM) provides excellent protection for data at rest and is easily implemented via a two-key system:
- DSM generates a unique data encryption key that encrypts all data within the volume.
- This key is then protected by a separate volume encryption key, which controls access to it.
Both keys are stored within the Encryption Key Vault, managed locally or externally on a separate device acting as a KMIP server. This ensures the encryption keys are kept safe, and administrators can enable auto-unlocking at startup or generate a recovery key in case of emergency, should the primary encryption keys be lost or damaged, to guarantee accessibility alongside strong security measures.
This layered approach to key management ensures that volume encryption on Synology systems provides strong protection against data breaches and loss.
Within the volumes are shared folders that serve as basic directories where authorized individuals can store and manage files and folders. Shared folder encryption works by locking down specific directories using an AES-256 key that can be centrally managed in Key Manager, making it easier to oversee multiple encrypted folders. Once a shared folder is encrypted, it remains inaccessible without its key, even if someone manages to extract the storage drives from the device.
| Feature | Volume Encryption | Shared Folder Encryption |
|---|---|---|
| Breadth | Volume encryption | Shared folder encryption |
| Impact on performance | All data within a volume | Specific folders |
| Complexity | Single key per volume | Single key per folder |
Keeping Backups and Cloud Storage Private
Synology’s encryption capabilities extend to backups and snapshots. Hyper Backup is DSM’s utility for backing up folders, system settings, and software packages from your Synology to another Synology device (on-premise) or C2 Storage (cloud). It performs end-to-end encryption through a dual-layered symmetric and asymmetric encryption approach that offers both speed and security, ensuring that your backups are protected during transfer and at rest.
Synology embeds data protection at multiple levels, from volumes to shared folders, the encryption framework ensures that sensitive data is fully protected with encryption keys that are generated, stored, and managed securely on the device itself or through trusted external vaults.
Snapshot Replication is a near-instantaneous data protection feature that allows you to “capture” your current data looks like. It’s like saving versions of documents you edit, but for entire folders. Combined with encryption, it is synonymous with having an encrypted time machine for your files, ensuring that your data is not only backed up but also protected from unauthorized access across its history.
We mentioned C2 Storage, Synology’s off-site cloud storage—the final piece of the golden 3-2-1 backup puzzle. As a public cloud service, C2 is designed to address the concerns of security and privacy-minded individuals with robust encryption mechanisms that protect data at every step, from NAS to data center.
Within C2 Storage itself, Synology’s Storage servers use AES 256-bit encryption, with the key kept on an entirely different system. Even Synology cannot access any of your data in transit or at rest.
| Feature | Encryption | Destination |
|---|---|---|
| Manual | None (unless implemented separately) | External hard drives, USB |
| Hyper Backup | AES-256, ECC Curve25519 | Another Synology device, C2 Storage |
| Snapshot Replication | AES-256 | Local storage, remote Synology NAS/SAN |
| C2 Storage | AES-256, TLS encryption (transport) | C2 Storage |
On a side note, those looking to securely synchronize data from their Synology devices to other cloud services like Google Drive can use Cloud Sync, another utility to keep their data safe.
Beyond Encryption
Now that we have briefly covered Synology’s encryption methods across different environments, it is essential to mention that encryption is not a panacea for data protection. Robust encryption is one part of the equation, and a more holistic approach to data protection is to include it with data replication and immutability technologies as part of your broader strategy for cyber resilience and data privacy.
Synology systems equip all of our users with a complete suite of tools designed to give you full data ownership and control, and that your data will remain secure, from edge to data center and to the cloud.