Japanese consumer electronics company Casio recently fell victim to a ransomware attack, causing widespread outages across the company. Casio’s company systems were down for a week, and employee and customer data were leaked.
As these types of cyber incidents occur with alarming frequency, organizations are becoming aware of the importance of data security and implementing preventative measures. From an IT perspective, protecting every piece of data is a mammoth task.
Daily maintenance of corporate data can be a pain, combining various hardware and software solutions can be inconvenient, the security posture might not meet audit requirements, and companies may be unable to ensure data accuracy.
These challenges make achieving 100% data protection for businesses nearly impossible.
This is why Synology has introduced ActiveProtect, a purpose-built backup appliance that secures data against ransomware and streamlines backup management.
Secure your backups to meet and exceed enterprise RPOs
As an integrated hardware and software backup solution, ActiveProtect streamlines the entire process as IT teams no longer have to assemble hardware and software components manually.
ActiveProtect comes with a built-in operating system that allows users to perform backups, replicate their data, eliminate duplicate copies of data via global source-side deduplication, instantly recover data, and perform multi-site management.
First, you need to ensure that your source data can be backed up quickly, efficiently, and accurately and that it can be fully restored. With global source-side deduplication, ActiveProtect reduces your backup times and bandwidth to boost performance and meet recovery point objectives (RPO).
ActiveProtect detects errors and corrupt data and repairs it with self-healing capabilities. Btrfs checksums continuously detect and repair data corruption via RAID to ensure zero errors.
To ensure data recoverability, companies can create a sandboxed environment within ActiveProtect to test their disaster recovery strategy without impacting their production environments.
Companies can also verify their backups by automatically generating a video to confirm that they can recover them in the event of a disaster. Businesses can recover entire systems, individual files, or perform physical-to-virtual (P2V) or virtual-to-virtual (V2V) restoration based on their recovery time objectives (RTO) in the event of a ransomware attack.
To minimize the impact of any ransomware attack, ActiveProtect supports local and off-site backups. These can be combined with immutable backups and WORM storage to ensure that no changes or deletions can be made to your data during the retention period.
Off-site backups are also encrypted before transmission to securely transfer your data to remote locations.
Preserve clean backup copies via offline backups
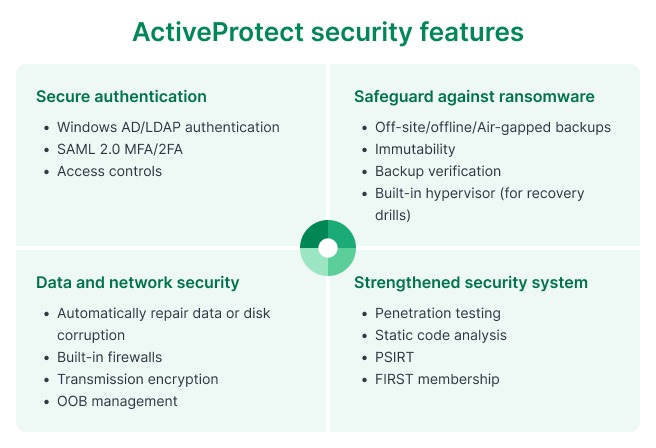
Assuming that backup servers are immune to ransomware, encryption threats, or data breaches is not the way to go. ActiveProtect’s robust security architecture focuses on three key areas:
1. Role-based access control
The principle of least privilege is enforced as a way to grant different types of permissions on the basis of a users’ role in the team.
As an example, IT infrastructure admins will only be able to manage hardware and network settings but will be unable to modify backup configurations. On the other hand, backup administrators will be able to adjust backup plans and access data stored on backup servers.
ActiveProtect also supports Windows AD and LDAP integration to reduce the burden on IT admins while following strict security policies.
2. Device access management
ActiveProtect allows companies to whitelist IP addresses to ensure that only devices with authorized IP addresses can access the backup server as a way to reduce the risk of a ransomware attack.
3. Physical isolation
In addition to following the 3-2-1 backup strategy, in which 3 copies of your data are stored on two different media and one copy is stored off-site, companies are encouraged to store an additional copy of their backup offline to strengthen data security.
Offline backups minimize the risk of cyberattacks, as servers are cut off from the network connection when data access isn’t required. This ensures that companies can immediately recover a clean copy of their data in the event of a ransomware attack.
ActiveProtect comes with multiple options for offline backups, such as automatically shutting down your hardware at designated times to completely isolate your server or setting up your network interface to block access to the server during non-specified hours.
Centralize your backups to boost operational efficiency
Streamline your data protection by ensuring data availability and backup infrastructure security so that IT admins can manage with ease and minimize time spent on routine operations.
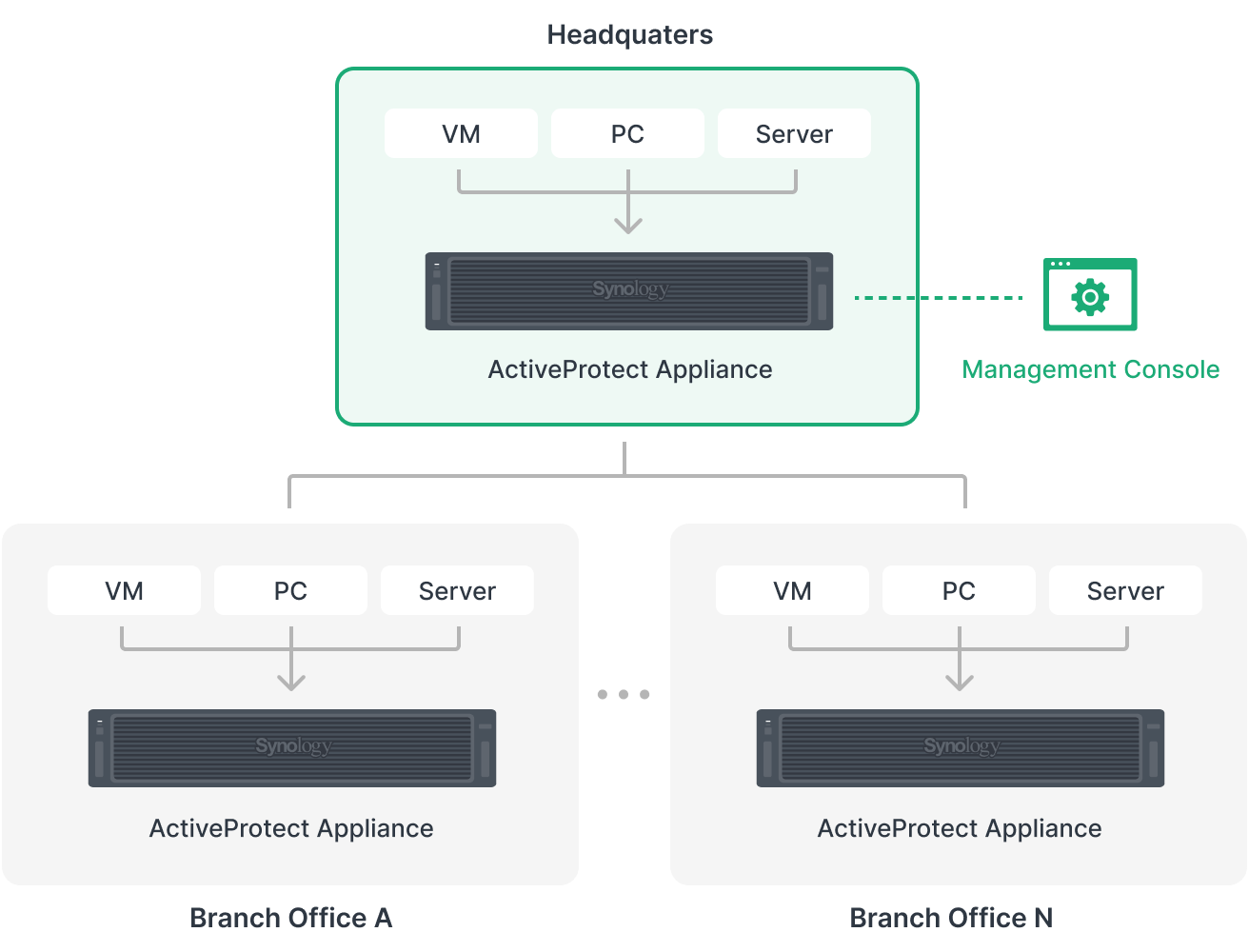
With a centralized console, ActiveProtect allows IT admins to oversee 2,500 servers and up to 150,000 workloads or manage your off-site servers.
ActiveProtect’s unified console showcases the entire backup infrastructure and the server status so that users can respond immediately in the event of a cyber attack.
For example, if a subsidiary is hit with a ransomware attack and their services are no longer running, IT admins from Headquarters can immediately check on the status of the subsidiary’s backup servers.
Even if the subsidiaries’ local backups have been affected, the company need not worry. You can quickly restore data from off-site backups at the Headquarters to maintain business continuity.
Conclusion
Defending cybersecurity has never been about one single step. It requires building a comprehensive data protection strategy. Synology ActiveProtect appliance is a secure, efficient and streamlined backup solution, perfect for businesses looking to simplify IT operations, ensure data integrity, and boost security measures.
As cyber threats continue to rise, leverage ActiveProtect to confidently safeguard your digital assets with continued business operations.
Take a look at Synology’s Data Protection Security Checklist to see if you’re doing enough to protect your data and read the Cyber Recovery Guide.