How a once enterprise-only technology was brought to Wi-Fi routers – and what challenges we have tackled.
Once upon a time, we protected ourselves against cyber attacks by installing antivirus programs on computers. Then we entered the IoT era in which everything is connected – even baby monitors and video doorbells can be hacked. Tech-savvy users have long learned to set up firewall rules, but no matter how granular they are, the rules are static by nature.
What if we can have automatic, network-wide protection that keeps itself up to date? This was the question we had in mind when designing the Synology Router Manager (SRM) 1.2. The answers were two new packages.
Safe Access & Threat Prevention: What are the differences?
The Safe Access and Threat Prevention packages, both available on Synology routers running SRM 1.2*, represent two different approaches to network security.
Safe Access is DNS- and IP-based. It integrates several external databases (including Google Safe Browsing) that identify domains and IPs related to malware, phishing, botnets, command and control servers, social engineering, etc. When a device in the network attempts to access the blacklisted destinations, Synology Router prevents the connection from even being established.
Threat Prevention, on the other hand, is signature-based. It monitors incoming and outgoing traffic using Deep Packet Inspection (DPI) – not just checking the domain or IP – and is able to drop any malicious packet detected in real time. In addition to Internet attacks, Threat Prevention can alert you to inappropriate user behavior, such as sending passwords through unencrypted HTTP traffic.
Both packages work automatically. You can review the event logs and adjust the actions, but even if you don’t, they still silently protect you in the background.
Nevertheless, there used to be another critical difference between them: performance.
Challenge: Enterprise technology comes at a cost
The technology behind Threat Prevention, called Intrusion Prevention System (IPS), has been an integral part of many enterprises’ security defenses. Because it inspects network packets using DPI, it can take a serious toll on the CPU and memory, dragging down the Internet speed overall.
Enterprises can afford an IPS because they can afford to use high-end hardware, some with purpose-built security processors. An enterprise firewall easily goes beyond US$1,000 – an exorbitant price for most homes and small offices. Therefore, when Synology first made IPS available on our Wi-Fi routers, users had to make a choice: business-grade security or Internet speed.
For most tech products, the story ends here: we live with the fact that we cannot always have the best of both worlds. Not this time, though.
How software changed the game
When building SRM 1.2, a huge amount of effort was dedicated to enhancing IPS performance. The key factors were CPU and memory usage, so after extensive research, the following changes were made:
- Revamped logging mechanism: The previous Intrusion Prevention Beta uses a spooler to process output data from the threat detection engine – this is how event logs are generated. However, it is also a CPU/memory-intensive program. We abandoned the old spooler and wrote a more efficient version on our own, significantly reducing the of system resources taken up by logging.
- Smarter packet analysis and detection: Not all packets are equal. When it comes to cyber attacks, there are parts of a network session specifically associated with them, such as the start of each session. By inspecting these parts for malicious packets, the engine is able to assess the risk of the entire session without having to go through every packet.
- Increased priority for the threat detection engine: In the previous version, the CPU and I/O priorities were set to very low to minimize the impact of IPS on the system. In a busy network, this sometimes results in the engine not being able to process the packets in time. After the changes above considerably lowered CPU and memory usage, we set the priorities back to normal.
So, what difference do they make?
We put both versions to test in the real world. Both were updated to use the same set of the latest signatures. The results show that the new Threat Prevention was able to detect a higher number of malicious events, as its lower CPU and memory usage enabled it to process significantly more connections per second (CPS).
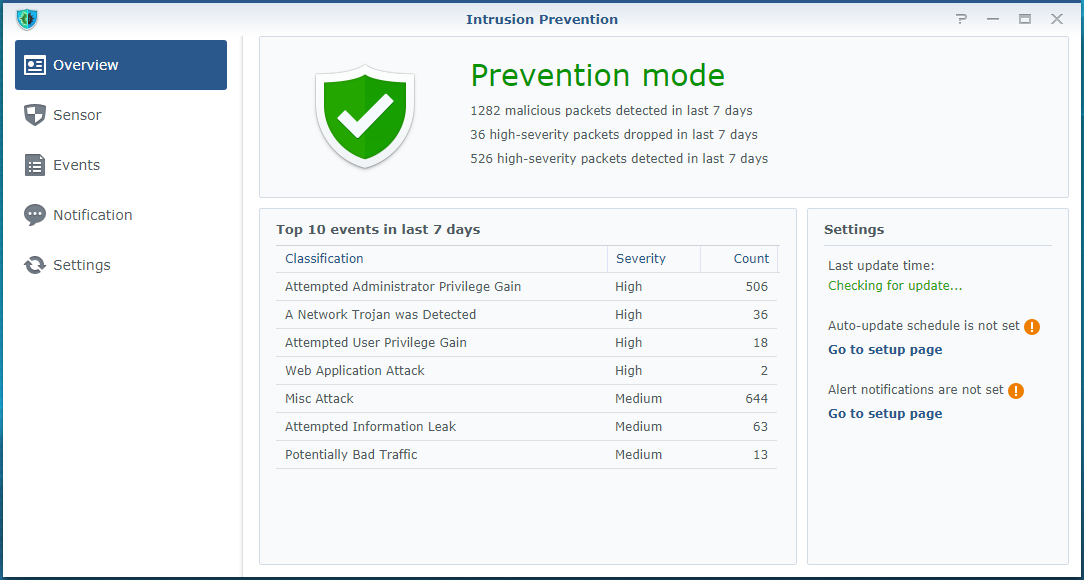
Fig. 1. Intrusion Prevention Beta in SRM 1.1: 1,844 events detected in seven days.
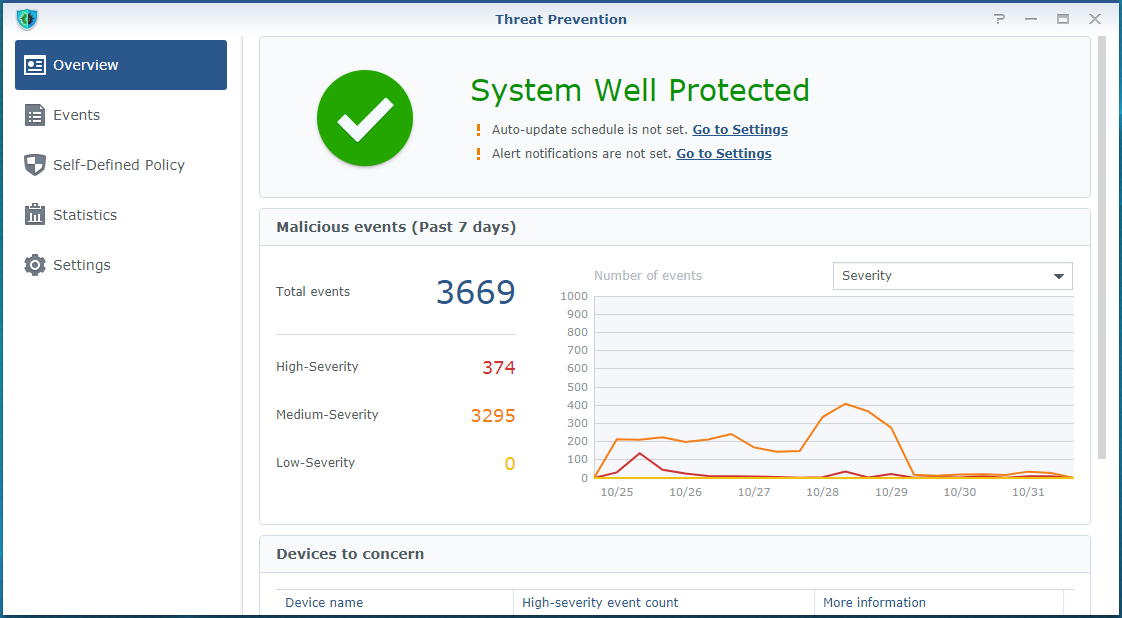
Fig. 2. Threat Prevention in SRM 1.2: 3,669 events detected in seven days.
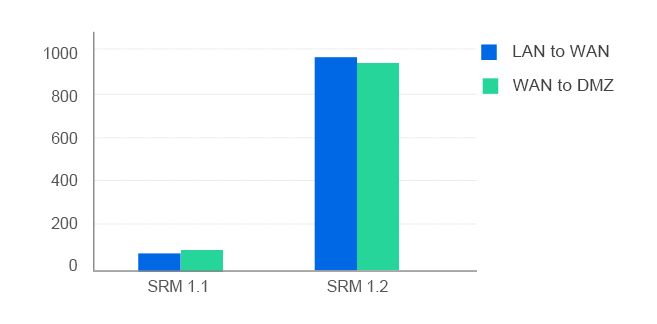
More importantly, it leads to a dramatic increase in performance. Take Synology RT2600ac as an example: the throughput jumped from sub-100 Mbps to close to Gigabit speeds. Similar results were observed on RT1900ac.
Fig. 3. Throughput comparison between Intrusion Prevention Beta in SRM 1.1 and Threat Prevention in SRM 1.2.
Why is this important?
According to Verizon’s report in 2018, only 1.8% of the security incidents were targeting small businesses, yet 34.1% of those that led to confirmed data breach had small businesses as their victims, meaning most of them had inadequate defenses comparing to enterprises. The same applies to home users.
IPS can provide an additional, effective layer of protection to most networks, which is why we put together all these efforts to optimize it for Synology routers – and we made that happen.
Are you using the security features in SRM 1.2? What do you think about network security on Wi-Fi routers in general? Tell us on Synology Community.
* Threat Prevention is currently available on Synology RT2600ac and RT1900ac.