Modern businesses today are facing unprecedented data security challenges. Rampant ransomware attacks, insider attacks, and malicious data deletions are occurring at an alarming rate. This could lead to corporate data vanishing overnight, causing significant financial losses and damaging corporate reputation.
Most organizations today have some form of data protection in place, but storing backups alone isn’t enough. If the backups are tampered with, deleted, or encrypted by hackers, there is a big possibility that businesses won’t be able to recover their data. This is why it’s important to go beyond backing up data and start protecting backups as well.
Companies often implement encryption or immutable capabilities to protect their backup data. Both are essential. However, both address fundamentally different levels of data protection. It’s crucial to understand the differences and how both can be used together to build a resilient data protection architecture.
Why encryption and immutability should be used together
Encryption is commonly used to protect data as it transforms data into an unreadable format. This is so that only authorized personnel with the correct encryption key will be able to access the data. With encryption, the goal is to enforce data privacy. Even if data is intercepted during transmission or accessed without authorization, the contents will be unreadable. This prevents leakage of trade secrets or personal data.
It’s important to note that encryption itself does not provide full data protection as it cannot prevent data deletion. As an example, backups themselves may become reencrypted in the event of a ransomware attack. This means that users will not be able to recover their data. Encryption guarantees that stolen data cannot be read by others. However, this does not mean that the data will always exist and can be restored successfully.
This is where immutability comes in. Encryption focuses on data privacy, while immutability ensures data existence. Immutable backups makes sure that data cannot be deleted or modified once it is written. When hit with malware attacks or accidental data deletion, backed up data is still clean and can be recovered. This removes the risk of data destruction and instead provides a safeguard for data recovery when facing a crisis.
| Encryption | Immutability | |
| How it works | Converts data into an unreadable format, which requires a key for decryption | Once written, data is locked and cannot be modified or deleted |
| What it does | Protects data privacy and prevents data from being readable if leaked | Ensures data existence and prevents deletion or tampering of data |
| Risk prevention | Data interception or unauthorized access of data | Prevents deletion or modification of data in the event of a ransomware attack |
| Purpose | Prevents misuse of stolen corporate or personal information | Ensures data remains recoverable after a disaster |
When dealing with ransomware attacks, immutability can serve as the foundation. This is because immutability can guarantee data integrity and availability. Encryption can serve as the secondary layer of defense as it prevents the exploitation of leaked data. Relying on a single defense method is no longer enough.
In today’s threat landscape, immutability and encryption must be combined to ensure data privacy and availability for businesses. This is the only way corporations can create a truly resilient backup architecture.
How Synology ActiveProtect integrates immutability and encryption to optimize performance and security
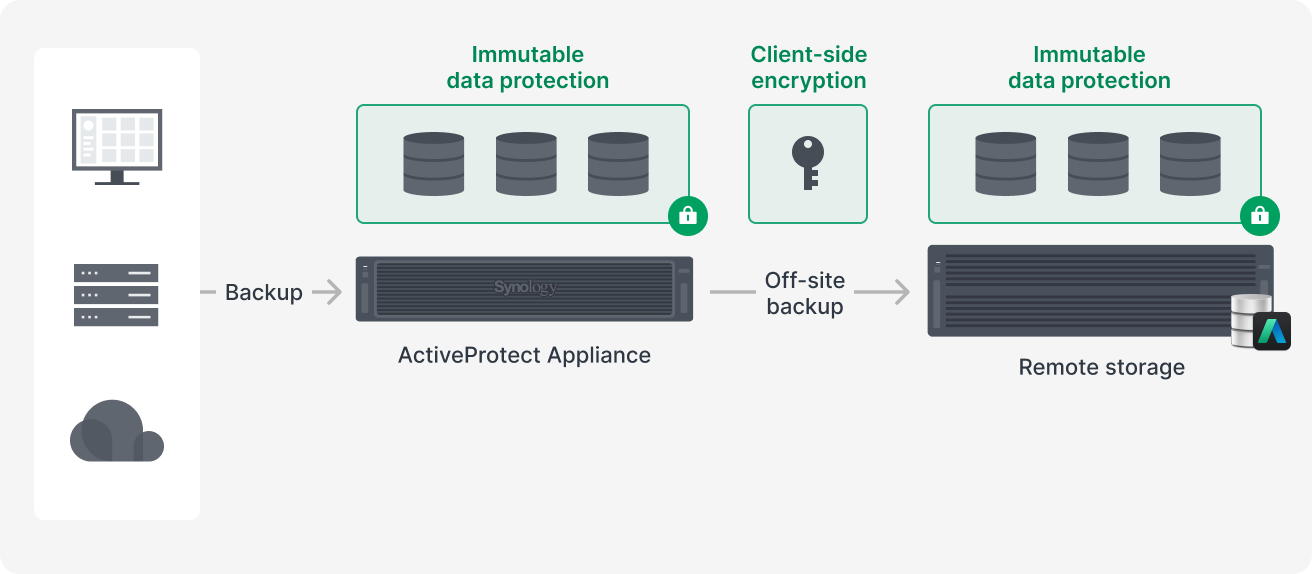
Synology ActiveProtect is an enterprise-grade backup appliance designed around data resilience and integrates both immutability and encryption within one unified backup architecture.
From creating backed up data to server storage to off-site data replication, ActiveProtect ensures immutable data protection. Client-side encryption is activated when data is transferred to a remote storage site. This means that the data is unreadable even if it is intercepted.
ActiveProtect is designed to meet real-world enterprise needs by including support for immutability and encryption.
Immutability is prioritized for local backup servers as the goal is to meet Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO) so that companies can perform backups quickly and restore data instantly in the event of a ransomware attack.
Write Once, Read Many (WORM) technology is used to lock data immediately after it is written as a way to prevent any data modification or deletion. This way, the CPU and I/O overhead are minimized as data isn’t repeatedly encrypted or decrypted during each backup. This helps to maintain both backup performance and data integrity.
In addition, ActiveProtect’s immutability comes with intelligent management capabilities so that the data is automatically locked in once the data is written. Users can set and manage retention policies via preset protection policies. During this time period, no data modification or deletion is possible. Once the lock expires, data is immediately archived.
In terms of remote storage, ActiveProtect extends immutability by adding AES-256 encryption for enhanced data protection. As off-site backups are typically stored to meet long-term data retention requirements and do not have to be frequently restored, performance matters less. What’s important is that data leaks are prevented during cross-site or cross-network data transmission. ActiveProtect uses client-side encryption to encrypt data before it leaves the backup server in order to mitigate this risk.
Optimized performance: Local backups skip repetitive encryption and decryption, allowing fast backups and restores to ensure business continuity.
Meet compliance requirements: End-to-end encryption is used for off-site data transmission and remote storage. This aligns with regulatory compliance such as GDPR and HIPAA for data privacy and reduces the chance of data leakage.
Dual-layer security mechanism: Built-in immutability prevents data tampering and deletion while encryption is used to safeguard privacy. This ensures that data remains intact and unreadable to unauthorized users.
In today’s complex world, it’s no longer enough to combat ransomware by relying on one piece of technology. ActiveProtect allows enterprises to leverage both immutability and encryption to ensure data integrity, privacy, and security. Both together create a dual defense method that enables rapid data recovery, helps businesses meet compliance, and ensure data resilience for the long term.
Click here to learn more about Synology ActiveProtect.