Generative Artificial Intelligence (GenAI) tools are revolutionizing the operations of businesses by offering the ability to quickly increase efficiency and solve complex problems. But this exciting potential comes with a significant challenge: data privacy.
In March, a Korean conglomerate lifted the ban on the use of GenAI, but reinstated it weeks later after employees shared sensitive internal information, including private code and a meeting recording. This incident highlights the need for organizations to leverage AI to increase productivity, while also managing and controlling data leakage risks.
Synology implements extensive de-identification techniques and rigorous safeguards in our workflow to prevent situations like this when leveraging advanced AI technologies. This ensures that customer information is handled responsibly and maintains high standards of data security and privacy.
Perform de-identification in a GDPR-compliant environment
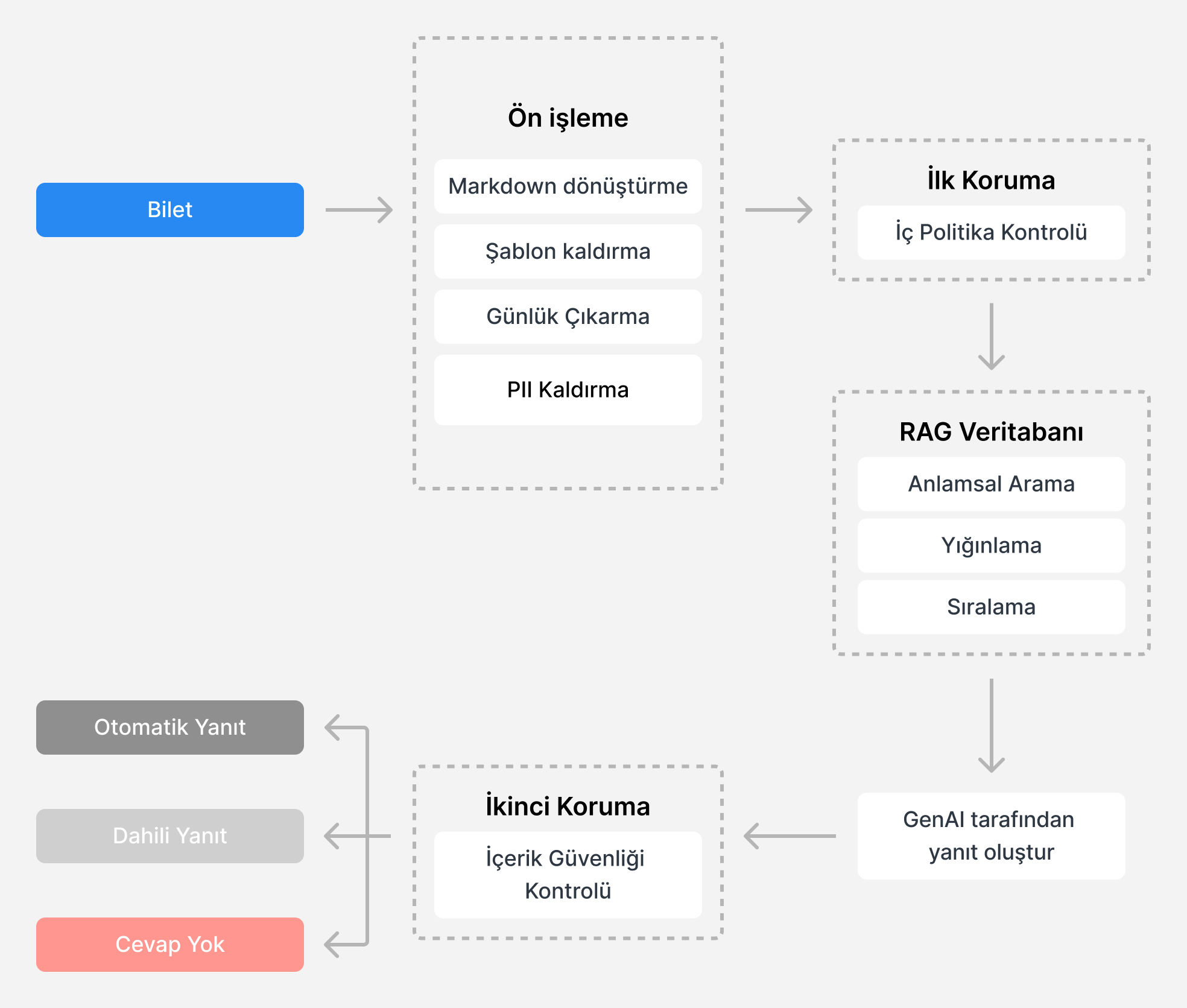
Synology has developed a Take-Back-Augmented Manufacturing (RAG) system to improve our technical support efficiency and accuracy. In addition, we have created a database of accredited support cases from the past year, providing up-to-date information specific to Synology products and solutions, certified by professional technical support engineers.
When a new request is received, the RAG system analyzes the customer’s question and retrieves the relevant solutions from the database, resulting in higher-quality responses compared to those produced by GenAI trained on the overall data.
This system is built on the foundation of protecting customer privacy, with a comprehensive de-identification mechanism that ensures that all data from past cases and newly received tickets is anonymized before use:
-
Regex Identification: Regular Expressions (Regex) identify patterns in support tickets, such as emails and phone numbers.
-
Named Entity Recognition (NER): Deployed with natural language processing to detect entities by understanding their context.
-
Checksum Validation: This ensures the accuracy of the patterns.
-
Context Analysis: Analyzes the surrounding text to increase detection confidence.
-
Anonymization Techniques: Ensures the security of detected sensitive information.
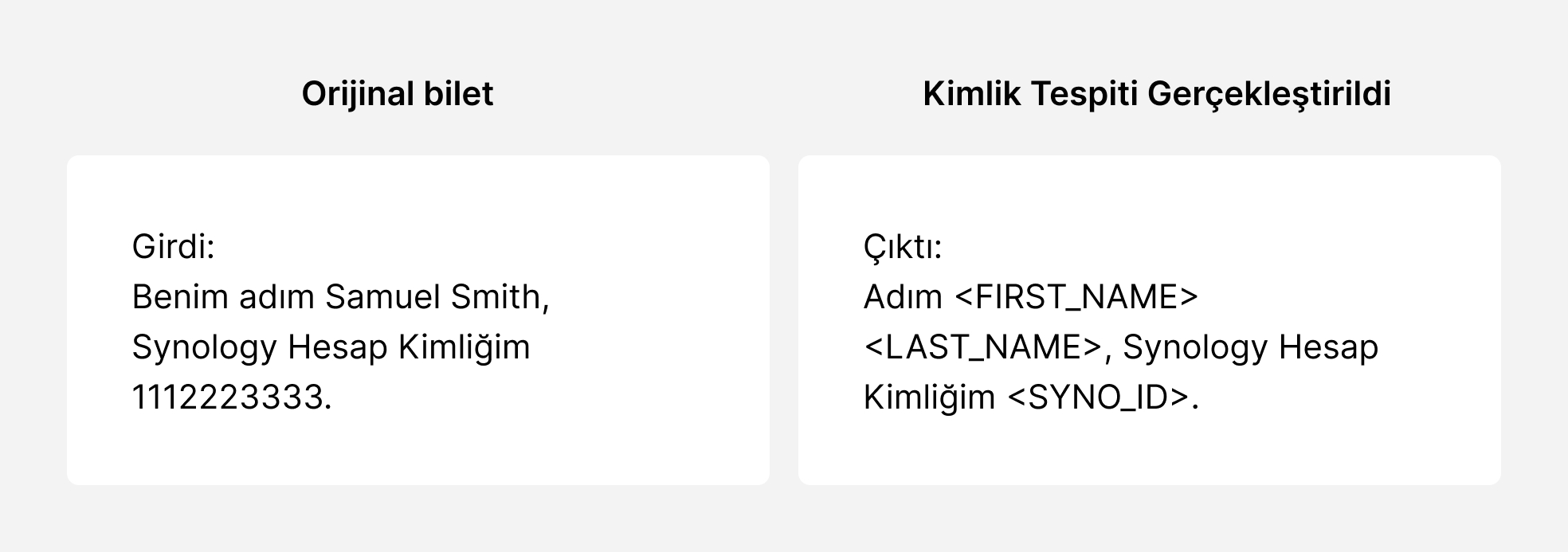
Most importantly, this comprehensive de-identification process is carried out in a GDPR-compliant environment, ensuring full regulatory compliance and data anonymization.
Prevent harmful or unwanted output with protective walls
After being reprocessed for de-identification, all AI-generated responses go through two guardrails in the system for policy checks to prevent accidental disclosure of sensitive information or potentially harmful recommendations.
-
Internal Policy Control: The initial firewall checks for internal policy violations or any risk of data loss for users. For example, if a support request requests installation files, DSM, or application versions that may affect users’ current environments, requests help with common vulnerabilities and exposure (CVE) issues, or refers to other support requests, the system stops responding and provides a summary of the main factors that drove the decision to the technical support engineer for a possible upgrade.
-
Content Security Check: The second firewall ensures that the generated responses do not provide sensitive information, such as console commands, remote access details, or other contextually accurate data that may not be available or inappropriate in certain scenarios. After passing this guardrail, the system will automatically decide whether to respond or forward the ticket to the support staff for review.
Sonuç
Yapay zeka destekli bu otomatik destek iş akışı, yanıt doğruluğunu ve alaka düzeyini önemli ölçüde artırarak yanıt sürelerimizi yirmi kat iyileştirdi. Titiz kimliksizleştirme süreçleri ve sağlam koruma duvarları uygulayarak veri gizliliğini sağlıyor ve katı gizlilik protokollerine bağlı kalıyoruz.
Yapay zeka destekli müşteri destek sistemini geliştirme deneyimimiz sayesinde, yapay zekanın güçlü sorun çözme yeteneklerine sahip olmasına rağmen, verimlilik ve gizlilik dengesini sağlamak için kontrol ve inceleme mekanizmalarıyla iyice sınırlandırılması gerektiğini tam olarak anladık. Synology ileriye dönük olarak gizlilik öncelikli taahhütlerini sürdürecek ve müşterilerin değerli verilerini korurken yapay zekanın potansiyelinden yararlanacaktır.
